ephemeral_vrf_sdk. Rollup programs call create_request_randomness_ix (the RequestRandomness instruction) with a caller_seed and a callback such as consume_randomness. An oracle from the EphemeralVrf network then executes the ProvideRandomness instruction to deliver the result.
Random numbers are generated via a VRF built on Curve25519’s Ristretto group and proven using a Schnorr-like signature as described in RFC 9381. The proof and output are returned to the rollup with a signed callback from the MagicBlock VRF signer PDA. Your program verifies the caller and then uses the randomness in gameplay logic.
Helper utilities like random_u32, random_u8_with_range, and random_bool make it simple to convert the [u8; 32] output into usable values. Because the request and consume steps occur inside the ephemeral execution window, users get real-time results with verifiable fairness and without relying on external servers.
Flow
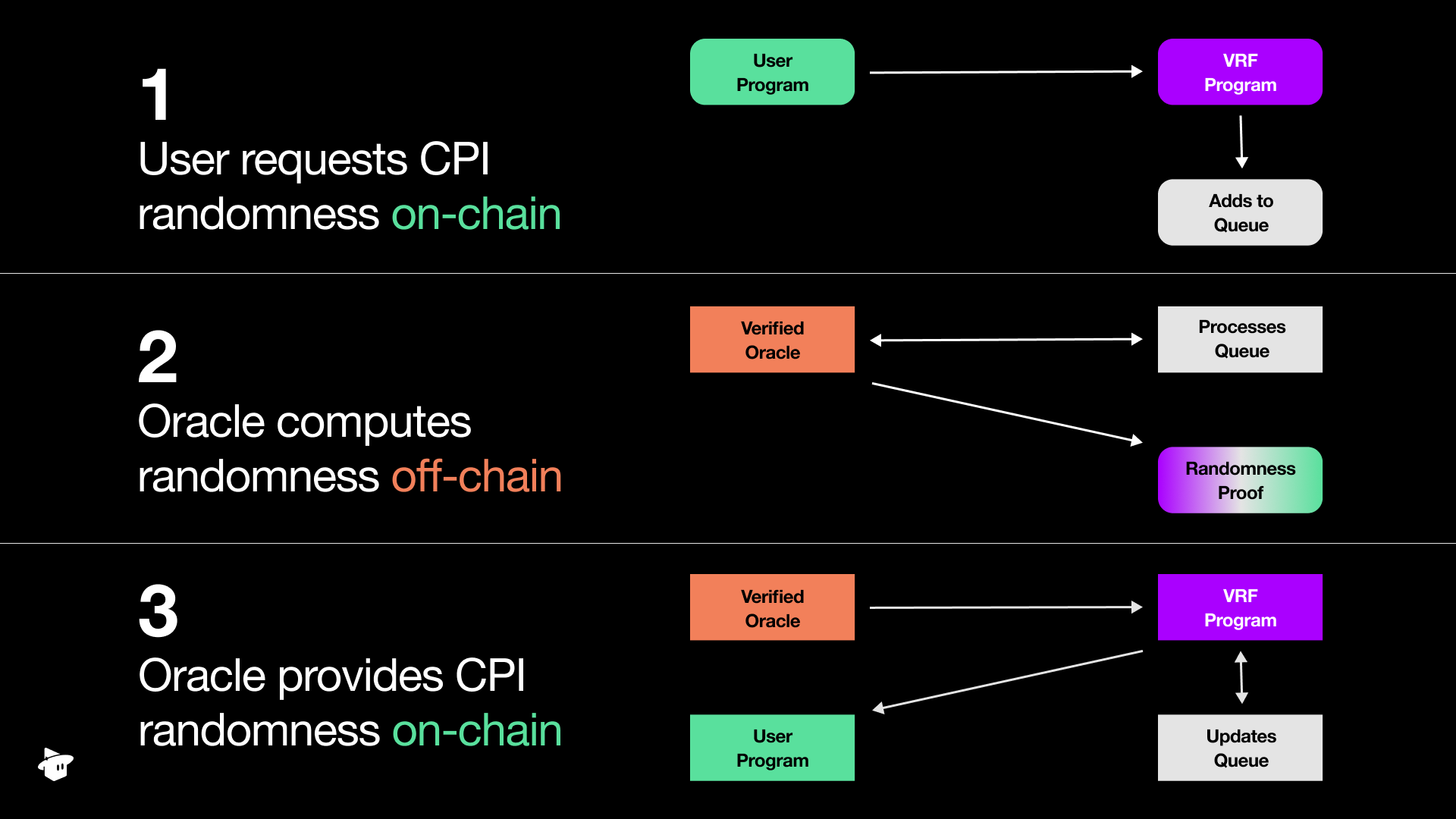
- Your program will CPI into the MagicBlock VRF program and append a request to the queue.
- Once your randomness request is in the queue, an oracle will release the request and perform the randomness computation.
- Upon completion, it returns the result and proof to the MagicBlock VRF program.
- After verifying the proof, the VRF program will call back into your program into a predefined function that will “consume” the randomness.
The EphemeralVrf codebase is still under active development and has not been
audited. Test thoroughly before integrating it into production rollups.

