randomness proof is verifiable onchain:
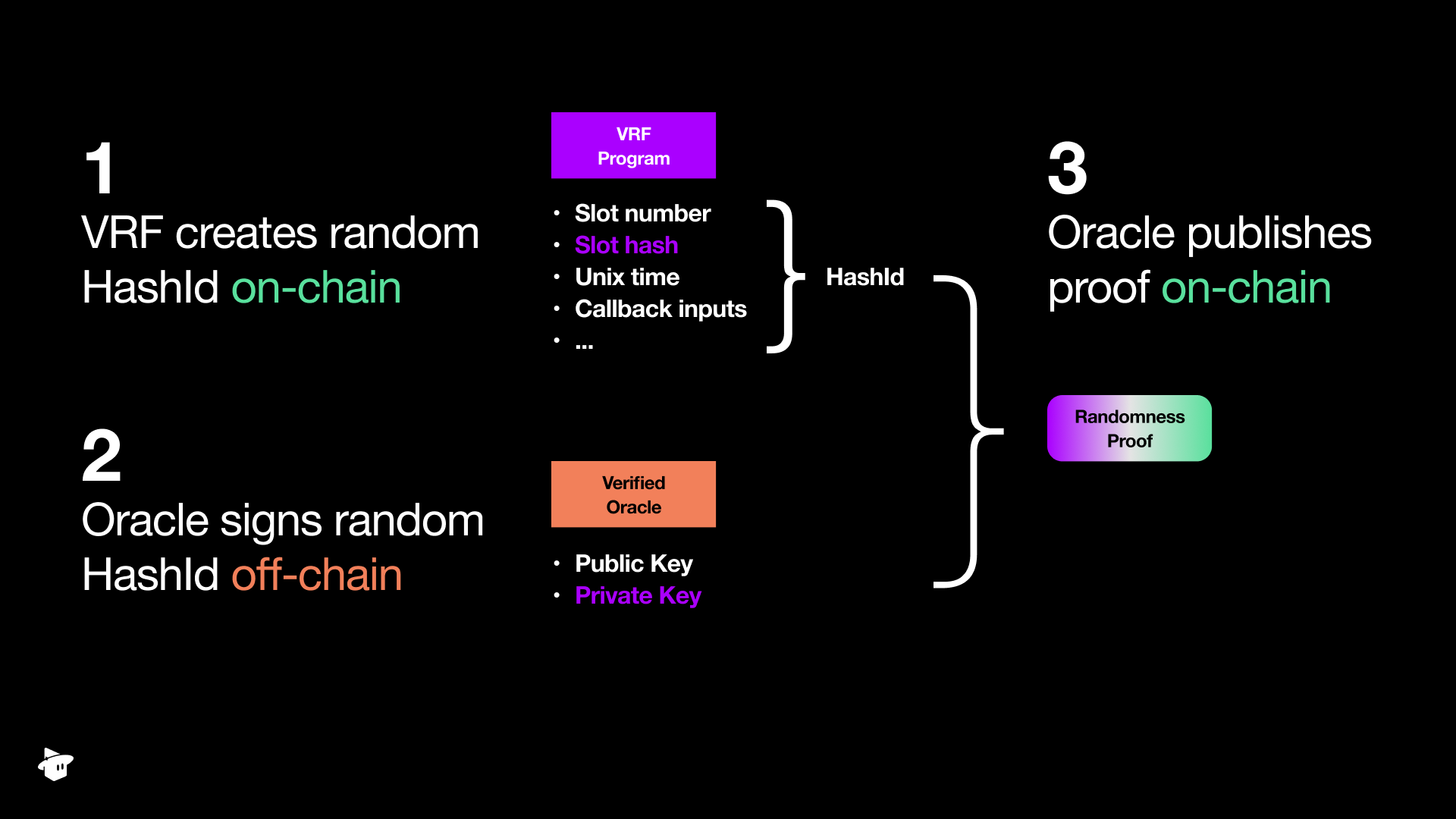
randomness proof is cryptographically bound to the input caller_seed and to MagicBlock’s VRF signer identity. Your callback enforces this with:
InvalidProof and Unauthorized so incorrect signatures or unauthorized callers are rejected before your game logic runs.
